Introduction
As time goes on, our world continues to become more networked, and more advanced sensors become part of the devices we use daily. Our cell phones, watches, and cars will soon be able to connect regularly with one another, creating a ubiquitous network of communication. This network can be used in a variety of ways. One such application is the detection and surveillance of unregulated Chemical, Biological, Radiological, Nuclear, and Explosive (CBRNE) materials. These detections are crucial for safeguarding the nation from weapons of mass destruction. Ubiquitous sensors can be used to detect some of these materials. By communicating detections in time and location, illicit materials can be localized, tracked, and ultimately interdicted.

Recent CBRNE threat at Boston Marathon 2013.
What is the problem and why is it important?
The United States’ susceptibility to a CBRNE attack has increased over the years due to prior terrorist intentions and events. From the 1990’s, the Department of Defense acknowledged both the creation of a growing number of CBRNE weapons of mass destruction and their impact on the United States. Since the terrorist attacks of September 11, 2001 and the Anthrax incident of 2001, there has been a heightened concern that nuclear weapons and chemical and biological materials pose a grave, future threat to the citizens of the United States. The Department of Homeland Security (DHS) was created to safeguard the country against terrorism and respond against these kind of attacks. In addition to smuggling hazardous materials into the country, there are several chemical agents that are easy to obtain and produce that can be used as weapons or explosives . Since the fear of chemical and radioactive agents getting into the wrong hands is so concerning and because of the detrimental effects of a CBRNE event or attack, it is a goal of the United States to focus their defense and security-related research toward the detection of explosive and chemical weapons that can be used as weapons of mass destruction.
Detection of explosive or chemical devices can be difficult due to the way they are concealed. Often, they are placed in crowded areas or main areas of travel so that it is difficult to be detected within the environment . More recently, explosive devices have been placed in overcrowded areas of high value and high visibility. In the United States, there are many public and transportation venues that are susceptible to a CBRNE incident. Such venues consist of, but are not limited to airports, sporting events, concerts, races, and speeches. Some examples from recent decades consist of the Boston Marathon tragedy, the World Trade Center bombings, and the New York City subway plot. Thus, it is extremely important to provide an appropriate sensor network framework and architecture to protect the people present at these and other similar events.
What did we do?
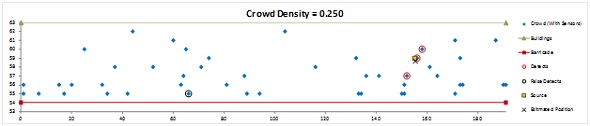
Our team has created a sensor network model in Excel Visual Basic that detects and localizes a single radioactive/nuclear source moving through an area. The model has three main variables: density, source strength, and sensor strength. The model was initially run with a base-case to analyze these three variables. Excursions were then run to compile data on the efficiency of the sensor network.
These excursions included: Increasing the randomness of the Source's Walk to the drop off point, Sensor's chance of a negative detection, Sensor's chance of a false detection, Chance for a crowd movement and varying sensor efficiencies.
The team analyzed the relationships between the input variables of the sensor network model and the outputs of the following metrics which including: Percent of Time Source is Seen, Average Error When Source is Seen, Maximum Error When Source is Seen, Last Position Error and Maximum Location Error.
What were our results?
From our analysis, we have created a framework for a (CB)RN(E) event interdiction using a ubiquitous sensor network. The framework takes into consider the variables that can be controlled, rather than those like crowd density (which can only be controlled to an extent) or source strength.
The preferred sensor is a strong one that can be dampened for a given density. For example, if a sensor sees a source, its strength can be dampened to better localize the source. Minimum sensor strength can be determined by source strength that is desired to be tracked. Reducing the chance of a negative detection occurring would be beneficial to a ubiquitous sensor network. This can be done by creating a manufacturing standard for all sensors that are placed within cell phones and other electronics.
There are three ways that false detections should be managed. Firstly, given a known sensor density attenuation range and number can be chosen in order to reduce false detections. Secondly, based on our analysis, false detections have a much greater effect on the network than negative detections. We suggest that in order to counter and reduce false detects, sensors have an internal capability of turning “off” or going into a “non-detect mode.” Once a sensor realizes that it is detecting when there is no threat, the sensor will cease to detect and become a negative detector. This will stop unnecessary data overload. A sensor realizes there is no threat by communicating with surrounding sensors. Lastly, as a look into the future, looking at the effects of other localization methods and multi targets are significant things that will aid in lowering error. This aspect is left for a future team to complete and analyze the model using multiple targets and exploring other localization models.
Distribution of sensor efficiency can’t be changed, however, randomized distribution can be created within an AD HOC sensor network. Sensors of varying efficiencies are better and dampening sensors will help create such a network. Adding larger sensors within the network is another way to make the sensor AD HOC with different strengths of sensors. With this dampening, random distribution creation can be achieved.